- Sophos Utm Exchange 2013 Web Server Protection
- Sophos Xg Firewalls
- Sophos Xg Community
- Sophos Xg Web Server Protection Software
- Sophos Xg Web Server Protection Windows 10
- Sophos Xg Web Server Protection Exchange
- Sophos Xg 210 Firewall
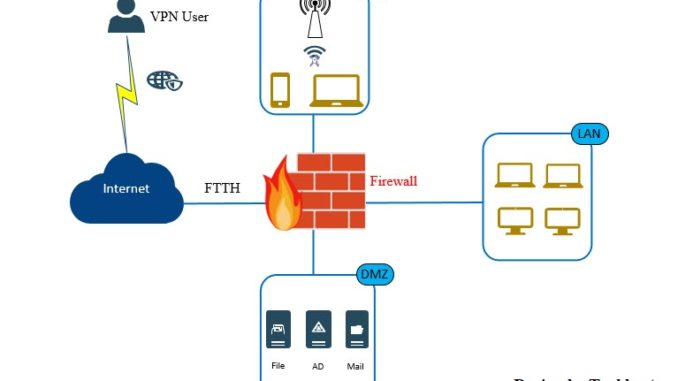
Web server You can protect web servers against Layer 7 (application) vulnerability exploits. These attacks include cookie, URL, and form manipulation. Use these settings to define web servers, protection policies, and authentication policies for use in Web Application Firewall (WAF) rules. XG Firewall acts as a reverse proxy, protecting your internal and external web servers. You can create WAF rules for IPv4 traffic. You can use the WAF rules to specify virtual web servers and translate these into physical servers without configuring DNAT and firewall rules.
With WAF rules, you can protect web applications from attacks and data leakage by filtering HTTP traffic.
 You configure a WAF rule for an IP address assigned to a network interface, a port, and one or more domain names.
You configure a WAF rule for an IP address assigned to a network interface, a port, and one or more domain names. Sophos Utm Exchange 2013 Web Server Protection
XG Firewall matches traffic based on the IP address assigned to the interface.For HTTPS traffic, it uses Server Name Indication (SNI) to determine the server that corresponds to the hostname in the client request.
- Go to Rules and policies > Firewall. Select IPv4 and select Add firewall rule.
- Rules are turned on by default. You can turn off a rule if you don’t want to apply its matching criteria.
- Enter the general details.
Name
Description
Rule name
Enter a name. Rule position
Specify the position of the rule.
Rule group
Specify the rule group to add the firewall rule to. You can also create a new rule group by using Create new from the list.
If you select Automatic, the firewall rule is added to an existing group based on first match with rule type and source-destination zones.
Action Select Protect with web server protection. Preconfigured template
Select a template to apply:
None: Specify the web server protection details.
Exchange Autodiscover
Exchange Outlook Anywhere
Exchange General
Microsoft Lync
Microsoft Remote Desktop Gateway 2008 and R2
Microsoft Remote Desktop Web 2008 and R2
Microsoft Sharepoint 2010 and 2013
- Enter the Hosted server details.
Name
Description
Hosted address
Select the public IP address assigned to an interface through which users access the internal server or host. The WAF rule is bound to the IP address assigned to the interface.
You can use the public IP address assigned to the interface or use an alias to bind the required public IP address.
When a client establishes a connection and accesses the web server, the web server obtains the interface address of the web application firewall (WAF) and not the client’s IP address. The HTTP header X-Forwarded-For carries the client’s IP address.
Listening port Enter the port number on which to reach the hosted web server. The defaults are port 80 for HTTP and port 443 for HTTPS.
You can use the same port (for example, 443) for SSL VPN and WAF. In this case, SSL VPN works on any IP address except the IP address (Hosted address) configured for WAF.
WAF can't share the same port as the user portal. The default user portal port is 443.
HTTPS
If you turn this on, the hosted server is accessible through HTTPS and not through HTTP.
HTTPS certificate If you selected HTTPS, select the certificate.
XG Firewall supports SNI (Server Name Indication), allowing you to create more than one virtual web server that's accessible over the same IP address and port. You can assign a different certificate to each server. Servers are presented to clients based on the requested hostname.
To create or upload a certificate, go to Certificates > Certificates.
Redirect HTTP Select to redirect port 80 traffic to port 443.
Domains
Enter the FQDN configured for the web server, for example, shop.example.com.
If you've turned on HTTPS, domain names of the selected HTTPS certificate show in the list. You can edit or delete these or add new domain names.
You can use the wildcard *. at the start of a domain name only.
Example: *.company.com
A single WAF policy supports multiple wildcard domains. Virtual web servers with wildcard domains are only matched when there are no virtual web servers with specific domains configured.
Example: A client request to the domain, test.company.com, will match with test.company.com before it matches with *.company.com before matching with *.com.
- Specify the details of the Protected servers. You can specify the web servers, authentication method, and allowed and blocked client networks. If you select path-specific routing, in addition to these settings, you can bind sessions to servers, specify the primary and backup servers, and use the WebSocket protocol.Note If you select multiple web servers, requests are balanced between the webservers.
If you don't want to configure path-specific routing, specify the Web servers and Access permissions.
Name
Description
Web server
Select the web servers from the Web server list. Alternatively, you can create new ones. You can see the selected web servers under Selected web servers. Allowed client networks Specify the IP addresses and networks that can connect to the hosted web server.
Blocked client networks Specify the IP addresses and networks to block from connecting to the hosted web server.
Authentication
Specify an authentication profile for web applications.
- Optional Select Path-specific routing to forward specific path requests to the selected web servers. For example, if you specify the domain www.test.com, the path /web, and the web server Web server 1, a request for www.test.com/web is forwarded to Web server 1.NoteXG Firewall doesn't evaluate requests based on the order of path listing. It applies the paths, starting with the longest path and ending with the default path route. The default path is used only if a more specific path doesn't match the request.Some instances in which you can specify path-specific routing are as follows:
- Send requests with a specific path (example: /products/) to a specific web server.
- Bind each session to a web server, using Sticky session cookie. Example: If you host an e-commerce site and want a single server to serve users for the duration of a shopping session.
- Send all requests to the specified web server with the others remaining as backup servers, using Hot-standby mode.
Name
Description
Default path (path /) Select the edit button and select a web server for the default path. Requests that don't match a listed path are sent to the default route. If you delete the default route, XG Firewall denies requests that don't match a listed path with a 404 Not found response.
Add new path
Select to add a new path.
You can add a path if you've added a web server.
Path
Enter the website path. Example:
/products/Web server Select the web servers from the Web server list. Alternatively, you can create new ones. You can see the selected web servers under Selected web servers. Authentication Specify an authentication profile for web applications. Allowed client networks Specify the IP addresses and networks that can connect to the hosted web server. XG Firewall only implements the protection for IP host type IP and Network. Don't specify an IP range or IP list.
Blocked client networks Specify the IP addresses and networks to block from connecting to the hosted web server.
XG Firewall only implements the protection for IP host type IP and Network. Don't specify an IP range or IP list.
Sticky session cookie
Turn it on to bind a session to a web server. XG Firewall forwards a cookie to the user’s browser, enabling it to route requests from the browser to the same web server.
If the server isn't available, the cookie is updated, and the session is switched to another web server.
Hot-standby mode
Turn it on to send all requests to the first selected web server. The other web servers remain as backup servers and are used if the first server fails.
When the main server starts functioning again, the sessions are switched back to it. If you select Sticky session cookie, the session continues with the backup web server.
WebSocket passthrough
Turn it on to allow applications hosted on the specified site path to use the WebSocket protocol.
Since RFC standards don't specify the protocol's data format, checks can't be implemented and WebSocket traffic is allowed without protection.
- Select Add new exception to specify the security checks to skip.
Select the paths, sources, and security checks to skip. You can specify more than one exception in a WAF rule.
Name
Description
Paths
Specify the paths for which you want to create an exception. You can use wildcards in the paths. Example: /products/*/images/*
Operation
Select the Boolean operation for paths and source networks. Sources
Specify the IP addresses, range, list, or networks from which the traffic originates. Cookie signing
Skips check for cookie tampering. Cookie signing mitigates attempts to obtain private session data and engage in fraudulent activity by tampering with cookies. When the web server sets a cookie, a second cookie is added to the first cookie containing a hash built from the name and value of the primary cookie and a secret that is known only to XG Firewall. If a request can't provide the correct cookie pair, the cookie is dropped.
Static URL hardening
Allows rewritten links for the specified paths and source networks.
Static URL hardening prevents users from manually constructing deep links that lead to unauthorized access. When a client requests a website, all static URLs of the website are signed using a procedure similar to cookie signing. In addition, the response from the web server is analyzed regarding which links can be validly requested next.
When you turn on static URL hardening, the entries for URL paths become case-sensitive. For example, if you add the path /rule.html and users enter /Rule.html, XG Firewall reports that the signature can't be found.
Form hardening
Skips checks for web form rewriting. To prevent tampering with forms, XG Firewall saves the original structure of a web form and signs it. If the structure has changed when the form is submitted, XG Firewall rejects the request.
Antivirus
Skips anti-virus scanning for requests from the specified source networks and to the paths that you specify.
Block clients with bad reputation
Skips checks for clients that have a bad reputation according to real-time blackhole lists (RBLs) and GeoIP information. - Specify the advanced protection policies.Name
Description Protection
Specify a protection policy for the servers.
Intrusion prevention
Specify an intrusion prevention policy.
Traffic shaping
Specify a traffic shaping policy to allocate bandwidth.
- Specify the Advanced settings.
Name
Description
Disable compression support
When clients request compressed data, XG Firewall sends data in compressed form.
Select this setting to turn off compression if web pages appear incorrectly or if users experience content-encoding errors. XG Firewall then requests uncompressed data from web servers and sends it to the client irrespective of the request’s encoding parameter.
Rewrite HTML
Select to rewrite the links of returned web pages to retain link validity.
Example: If a web server's hostname is yourcompany.local, but the hosted web server’s hostname is yourcompany.com, absolute links like [a href='http://yourcompany.local/'] are broken if the link is not rewritten to [a href='http://yourcompany.com/'] before delivery to the client.
You don't need to select this option if yourcompany.com is configured on your web server or if internal links on your web pages are always realized as relative links.
We recommend that you use the option with Microsoft Outlook web access or SharePoint portal server.
HTML rewriting affects all files with HTTP content type text/* or *xml*. * is a wildcard. To prevent corruption during HTML rewriting, make sure that other file types (example: binary files) have the correct HTTP content type.
Rewrite cookies
Select to rewrite cookies of the returned web pages.
Pass host header
Select to forward the host header requested by the client to the web server.
You can use this to match the requested hostname with the web server when you've hosted more than one website on a server.
- Click Save.When you save a new or edited web server protection rule, XG Firewall restarts all web server rules. Live connections using any of these rules will be lost and need to be re-established.
Sophos Xg Firewalls
- In the Sophos XG management console click Log Viewer in the top right. Select Web server protection on the right-hand drop down box and you should see an entries similar to the image below We can see an error entry for WAF anomily when the Protection Policy is enabled. We can see a normal log entry for when the Protection Policy is set to none.
- Sophos XG Firewall is the only network security solution that is able to fully identify the user and source of an infection on your network and automatically limit access to other network resources in response.

Sophos Xg Community
Sophos Xg Web Server Protection Software
WAF rules allow you to control the HTTP traffic of a web application over the IPv4 protocol.
Sophos Xg Web Server Protection Windows 10
You can configure more than one WAF rule on a given network interface or port, using different hostnames and certificates. With support for Server Name Indication (SNI), web server protection will present the correct server to each client, based on the requested hostname.
Sophos Xg Web Server Protection Exchange
- Go to Firewall and select IPv4 using the filter switch.
- Click + Add firewall rule and Business application rule.
- Enter the general rule details.
Application template
Select Web server protection (WAF) to define an application filter policy for HTTP based applications.
Rule name
Enter a name for the rule.
Description
Enter a description for the rule.
Rule position
Specify the position of the rule.
Rule group
Specify the rule group to add the firewall rule to. You can also create a new rule group by using Create new from the list.
If you select Automatic, the firewall rule will be added to an existing group based on first match with rule type and source-destination zones.
- Enter Hosted server details.
Hosted address
Select the interface of the hosted server to which the rule applies. It is the public IP address through which internet users access the internal server/host.
When a client establishes a connection and accesses the web server, the web server does not obtain the client’s real IP address. The server obtains the address of the interface used by the web application firewall (WAF) because the connection is made through the WAF. The client’s real IP address is available in the HTTP header
Listening port Enter a port number on which the hosted web server can be reached externally over the internet. Default is port 80 for plaintext communication (HTTP) and port 443 for encrypted communication (HTTPS).
HTTPS
Select to enable or disable scanning of HTTPS traffic.
HTTPS certificate Only with HTTPS.
Select the HTTPS certificate to be used.
Redirect HTTP Only with HTTPS.
Select to redirect HTTP requests.
Domains
HTTPS disabled: Enter the FQDN configured on the web server, for example, shop.example.com.
HTTPS enabled: Depending on the HTTPS certificate you select, some domains may be preselected. You can edit or delete these domains or add new ones.
- Specify Protected server(s) details.Path-specific routing
You can enable path-specific routing to define (a path) to which web servers incoming requests are forwarded.
You can define that all URLs with a specific path, for example, /products/, are sent to a specific web server. On the other hand you can allow more than one web server for a specific request but add rules how to distribute the requests among the servers. Additionally, you can define that each session is bound to one web server throughout its lifetime (sticky session). This may be necessary if you host an online shop and want to make sure that a user sticks to one server during the shopping session. You can also configure to send all requests to one web server and use the others only as a backup.
For each hosted web server, one default site path route (with path /) is created automatically. The device automatically applies the site path routes in the most reasonable way: starting with the strictest, that is, longest paths and ending with the default path route which is only used if no other more specific site path route matches the incoming request. The order of the site path route list is not relevant. If no route matches an incoming request, (in case the default route was deleted), the request will be denied.
Add new path
(Only available if Path-specific routing is selected. Only active after at least one web server and one hosted web server have been created.) Click Add path to define a new path.
Web server
(Not available if Path-specific routing is selected.)
With this option, you select the web servers that are to be protected. Select a web server from Web server list. The selected web server is displayed on the right side of the table under Selected web server(s).
A new web server can be created on the Web server > Web servers page.
- Specify Access permission details. (Not available if Path-specific routing is selected.)Allowed client networks
Select or add the allowed networks that should be able to connect to the hosted web server.
Blocked client networks Select or add the denied networks that should be blocked to your hosted web server.
Authentication
Select a web app authentication profile or click Create new to create a new authentication profile.
- Add path Exceptions for the web servers.
Click Add new exception to specify a new exception.
- Specify policies for business applications in the Advanced section.
Protection
Select an application protection policy for the server or create a new one.
Intrusion prevention
Select an intrusion prevention policy for the rule or create a new one.
Traffic shaping
The traffic shaping policy allocates and limits the maximum bandwidth usage of the user.
- Specify additional options for the added server in the Advanced section.
Disable compression support
By default, this check box is disabled and the content is sent compressed when the client requests compressed data. Compression increases transmission speed and reduces page load time. However, if websites are displayed incorrectly or users experience content-encoding errors when accessing your web servers, it may be necessary to disable compression. When the check box is enabled, the WAF will request uncompressed data from the web servers of this hosted web server and will send it uncompressed to the client, independent of the HTTP request’s encoding parameter.
Rewrite HTML
Select this option to have the device rewrite links of the returned web pages in order for the links to stay valid. Example: One of your web server instances has the hostname yourcompany.local but the hosted web server’s hostname on the device is yourcompany.com. Thus, absolute links like [a href='http://yourcompany.local/'] will be broken if the link is not rewritten to [a href='http://yourcompany.com/'] before delivery to the client. However, you do not need to enable this option if either yourcompany.com is configured on your web server or if internal links on your web pages are always realized as relative links. It is recommended to use the option with Microsoft’s Outlook web access and/or SharePoint portal server.
HTML rewriting affects all files with a HTTP content type of text/* or *xml*, where * is a wildcard. Make sure that other file types, for example, binary files, have the correct HTTP content type, otherwise they may get corrupted by the HTML rewriting process.
Rewrite cookies
Select this option to have the device rewrite cookies of the returned web pages.
Pass host header
When you select this option, the host header as requested by the client will be preserved and forwarded along with the web request to the web server. Whether passing the host header is necessary in your environment depends on the configuration of your web server.
- Click Save.As soon as a new HTTP-based rule configuration has been created and saved or an existing HTTP-based rule configuration has been altered and saved, all HTTP-based business rules will be restarted. Any underlying client connection using a HTTP-based business rule will get lost and has to be re-established.
Sophos Xg 210 Firewall




