When you have enabled Domain pass-through and User name and Password authentication on Receiver for Web, the first time a user logs on they get this prompt to either log on using the account used to sign on to the computer or to switch to the username and password logon screen. The user name and password logon screen gives the user the ability to authenticate with any set of credentials they have. Citrix Workspace Enable Single Sign-on When enabled, single sign-on remembers your credentials for this device, so that you can connect to other Citrix applications without having to sign in each time. You should do this only if your IT administrator has instructed you to. This will take effect the next time you log on to this device. A single place to simplify delivery of Citrix technologies. Provide secure access to apps, data and IT tools. Deploy on any cloud or infrastructure. Citrix Federated Authentication Service (FAS) supports single sign-on to virtual apps and desktops in Citrix Workspace. Within each resource location, you can connect multiple FAS servers to Citrix Cloud for load balancing and failover purposes. You can use the same FAS server for both on-premises and Citrix Cloud with proper rule configuration. Citrix Workspace app with passthrough (Windows Domain Joined) Citrix Workspace app with passthrough (Mac Domain Joined) By the end of this blog, you should have a good understanding of how with Citrix Workspace + Okta you can deliver an experience that will make your users want to use the Workspace.
One of the challenges with using cloud services is getting the same experience you had in an on-premises deployment.
For the past 20+ years, many Citrix Virtual Apps and Desktop deployments utilized a Citrix Gateway to provide an ICA proxy through the firewall. For external users, Gateway also authenticated those users. Over the years, admins determined the authentication schema for their organization, most likely incorporating additional factors beyond passwords, like TOTP, certificates, RADIUS, nFactor, etc.
Fast forward to 2019 and we now need to figure out how to use Citrix Workspace without impacting our secure authentication profile.
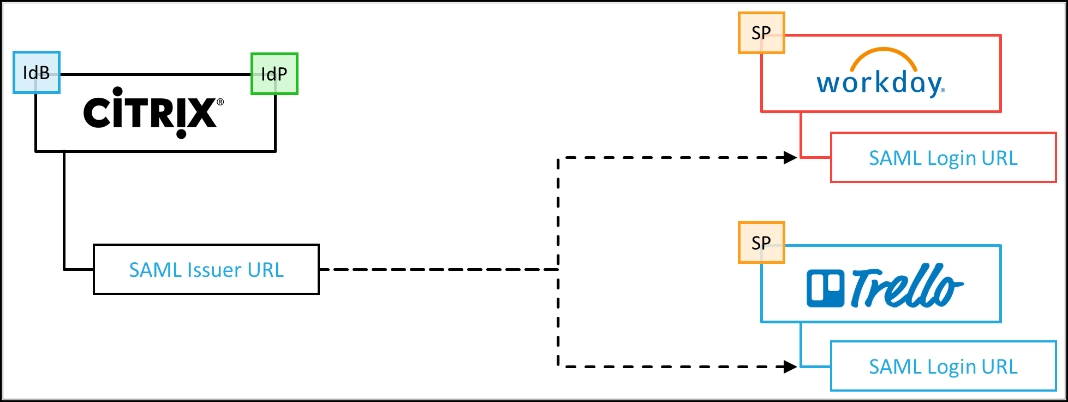
Currently in tech preview, the identity portion of Citrix Workspace includes an option to utilize an on-premises Citrix Gateway as the Workspace’s IdP.
Workspace essentially redirects the authentication requests to the Gateway’s FQDN. When the Gateway authenticates the user, it replies to Workspace with the Active Directory account information, to be used to single sign-on users to additional Windows-based resources (virtual apps and desktops).
Integrating an on-prem Citrix Gateway into Citrix Workspace is fairly straight-forward and can be seen in the latest Tech Insight video:
Authentication Blog Series:
Daniel (Twitter @djfeller)
Hi everyone
I've built two identical virtual machines, built using the same steps, and with the same configuration, apart from one being installed with Windows 10 Enterprise, and the other being installed with Windows 10 Education. My understanding is that the functionality (in the UK at least) is identical for the two versions. They both reside in the same Active Directory OU. Windows is auto-activated with both editions on Windows 10 by the on-prem KMS Services.
I've then installed the latest CitrixWorkspaceApp.exe onto both using the command
CitrixWorkspaceApp.exe /includeSSON ENABLE_DYNAMIC_CLIENT_NAME='Yes'
I've then applied a GPO that specifies the default StoreFront server to connect to, sets the 'Use Local username and password' settings, display Applications on Desktop, etc.
(NOTE: I'm using http to connect to storefront, not https, but I've set the required registry key to allow this)
On the Windows 10 Enterprise edition, the published apps and desktops appear correctly on the desktop and start menu.
On the Windows 10 Education edition, nothing appears on the desktop or start menu, and it appears that Citrix Workspace App is not performing single sign-on to StoreFront.
In Workspace Apps' Advanced Properties, running Configuration Checker/SSONChecker, on Windows 10 Enterprise, I get the following
----------- Citrix Workspace Config Check Results ---------
[Test Provider:SSOnChecker.dll]
[SSONChecker][Installation][Installed with Single Sign-on][Checking that Single Sign-on was enabled when installing Citrix Workspace.]
[SSONChecker][Installation][Sign-In credential capture][Checking that Citrix Workspace's configuration allows your desktop sign-in credentials to be re-used for single sign-on.]
Citrix Workspace App Enable Single Sign On
[SSONChecker][Installation][Network Provider registration][Problems may occur if Single Sign-on is not the first accessed Network Provider. Edit provider order in system Network Connections, Advanced Settings.]
[SSONChecker][Installation][Single Sign-on process running][Checking that the Single Sign-on process is running.]
[SSONChecker][Group Policy][Group Policy][Checking that 'Local user name and password' Group Policy is enabled or left not configured.]
[SSONChecker]['School Service' store configuration][Internet settings for 'School Service (http://storefront.xxxxxxxxx.net/Citrix/Store/resources/v2)'][Checking for the 'automatic sign-in' right for the security zone of the store's URL.]
[SSONChecker]['School Service' store configuration][Auth methods for 'School Service (http://storefront.xxxxxxxxx.net/Citrix/Store/resources/v2)'][Checking that domain passthrough authentication is enabled for the store.]
Running exactly the same test on Windows 10 Education I get
----------- Citrix Workspace Config Check Results ---------
[Test Provider:SSOnChecker.dll]
Citrix Workspace App Single Sign On Account
[SSONChecker][Installation][Installed with Single Sign-on][Checking that Single Sign-on was enabled when installing Citrix Workspace.]

[SSONChecker][Installation][Sign-In credential capture][Checking that Citrix Workspace's configuration allows your desktop sign-in credentials to be re-used for single sign-on.]
[SSONChecker][Installation][Network Provider registration][Problems may occur if Single Sign-on is not the first accessed Network Provider. Edit provider order in system Network Connections, Advanced Settings.]
[SSONChecker][Installation][Single Sign-on process running][Checking that the Single Sign-on process is running.]
[SSONChecker][Group Policy][Group Policy][Checking that 'Local user name and password' Group Policy is enabled or left not configured.]
I.e. the last two lines aren't shown, implying that it's not finding the pre-configured store settings, although the values are stored in the registry after manually checking (the reside in the same OU so have the same GPO applied)
If anyone's seen anything similar and knows a fix (other than deploying Enterprise instead of Education), please let me know.
Regards
Ken Z




