As a license bundle, Microsoft 365 E3 combines Office 365 E3, Enterprise Mobility + Security (EM+S) E3, and Windows 10 Enterprise E3. It’s the way to go if you want to add advanced security features to you O365 workloads and you also need a Windows 10 Enterprise license anyway.
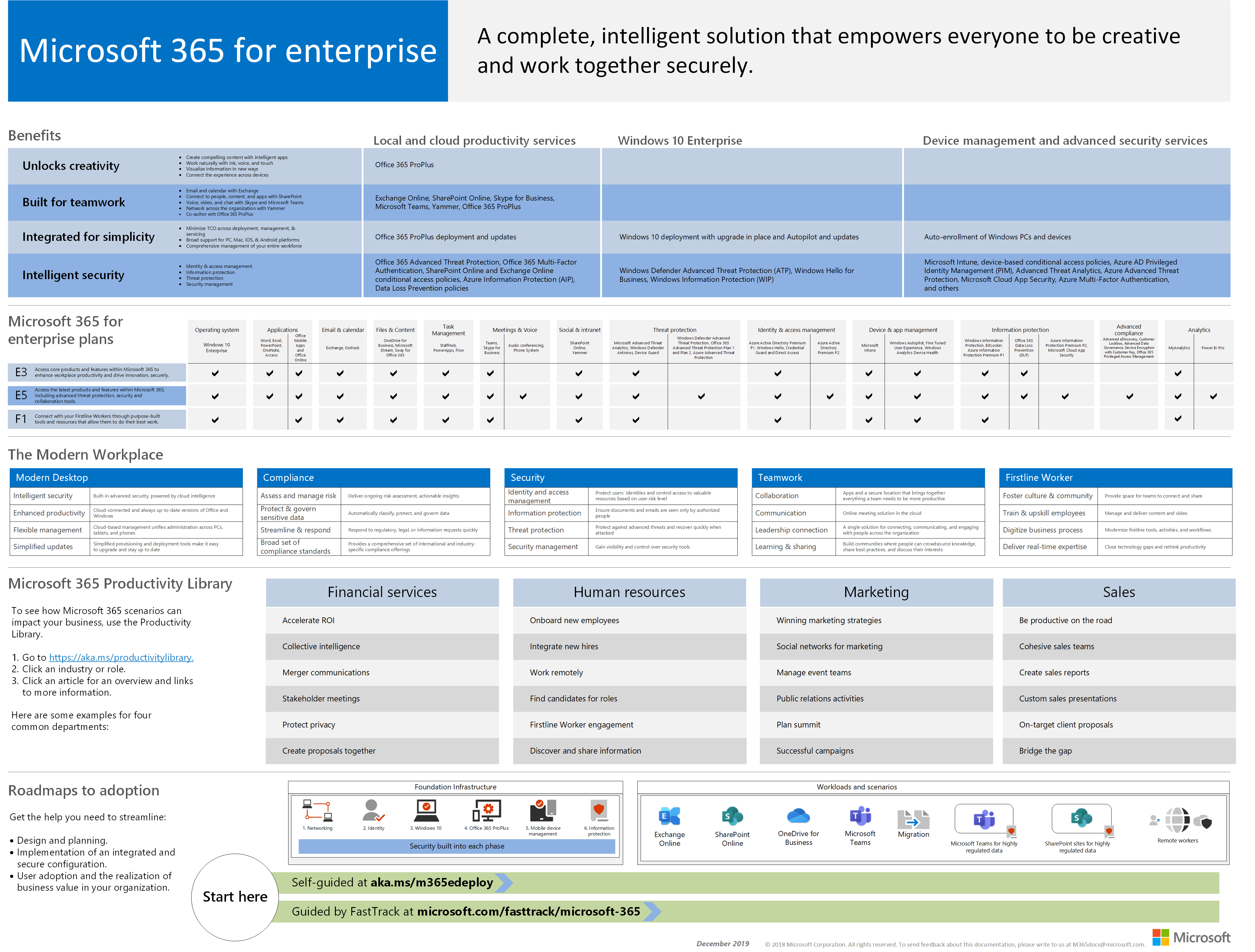
From the Microsoft 365 compliance center, use Data classification Overview to monitor how your retention labels are being used in your tenant, and identify where your labeled items are located. For more information, including important prerequisites, see Know your data - data classification overview. Microsoft 365 E5 Insider Risk; Microsoft 365 E3 users can use these add-ons to take advantage of some of the additional features Microsoft 365 E5 includes. For more information, see Features and capabilities for each plan. Get the big picture. The Microsoft 365 for enterprise poster is a central location for you to view.

- Microsoft 365 E5 Insider Risk; Microsoft 365 E3 users can use these add-ons to take advantage of some of the additional features Microsoft 365 E5 includes. For more information, see Features and capabilities for each plan. Get the big picture. The Microsoft 365 for enterprise poster is a central location for you to view.
- Sep 30, 2020 There are price differences between Microsoft 365 E3 and Office 365 E3. Microsoft 365 E3 is $32 per user, per month, while Office 365 E3 is $20 per user, per each month.
- How to activate and assign Office 365 (E3) internal-use rights licenses. For your reference: renew internal office 365 licenses via action pack. If you need further help and if you are an MPN Partner, please contact Microsoft Partner Support for further assistance. Contact Microsoft Partner Support.
If you want to get to know the additional capabilities of Microsoft 365 E5 visit my other post: Microsoft 365 E5 security baseline.
What you get (security related)
Office 365 E3 security baseline
- Configure anti-malware and anti-spam policies for basic mail protection. Implement SPF and DKIM to use authentication for your domains.
- Enable Office 365 auditing
- Enable Office 365 mailbox auditing
- Check Office 365 Secure Score on a regular basis but do not rely exclusively on it! Some things are not covered and probably never will.
- Use SharePoint / OneDrive for Business Access Controls to limit potential data loss.
EMS E3 / Azure AD security baseline
- Use dedicated administrative accounts for Office 365 and Azure AD. Make sure that on-premises admin accounts are NOT cloud enabled.
- Implement Multi-factor Authentication for all administrative accounts
- Hybrid join Windows 10 devices to use them as known devices
- Use Device Writeback to implement Windows Hello for Business in hybrid mode
- Implement Multi-factor Authentication for standard users. Build a sufficient strategy based on known devices and locations by leveraging Conditional Access. If users are forced to confirm prompts at every logon, they will most likely do so for sign-ins they did not perform
- Use Conditional Access to limit cloud usage. Use known locations, known devices, and approved client apps to make sure an attacker would also need other factors besides username and password to gain access
- Get rid of legacy authentication
- Block Exchange ActiveSync and switch to modern authentication mail clients
- Regularly check Azure AD sign-in logs for failed authentication to get a feeling on how affected your tenant is by password spray attacks
- Monitor Azure AD Connect Health status including ADFS failed sign-ins (if you use federation)
- Monitor Azure AD app registrations
- Use Cloud App Discovery (sub-function of Microsoft Cloud App Security) to discover cloud app usage.
- Limit external access and guest users depending on your use cases
- Use Intune to prevent data leakage on mobile devices by leveraging either Intune App Protection (app containers) or a fully-managed implementation for Android and iOS
- Evaluate Azure Information Protection to protect corporate data. Start with a simple approach that allows users to get a feeling for how it works. Extend your deployment once you get an overview about the impact AIP has for users and how data is handled inside your organization.
- Deploy Microsoft Advanced Threat Analytics to monitor your on-premises Active Directory for known attacks like Pass-the-Hash, Pass-the-Ticket, and many others.
Windows 10 Enterprise E3 security baseline

Microsoft 365 E3 Comparison
Expand your existing Windows 10 settings to leverage enhanced security features:
- Limit local administrative rights, users should work as standard users per default
- Randomize des built-in Administrator account, e.g. using LAPS (Local Administrator Password Solution)
- Make sure all devices come with a Trust Platform Module (TPM) version 2.0. Version 1.2 is fine for existing devices.
- Install devices in UEFI mode with Secure Boot enabled
- Activate virtualization capabilities
- Protect UEFI settings from unwanted changes
- Use BitLocker with a TPM for volume encryption. Protect from DMA attacks by either using a startup PIN or DMA protection which is now included in Windows 10.
- Activate Credential Guard to protect the LSASS process. Start without UEFI lock for fallback, switch to UEFI lock once you get comfortable with manually reseting UEFI variables, which is needed to deactivate Credential Guard
- Implement client isolation by leveraging the Windows Firewall. Clients mostly never need to communicate with other clients unsolicitedly
- Activate User Account Control, SmartScreen, and Network Protection
- Use Application Control (or AppLocker) and Exploit Guard at least in audit mode. Audit data can be evaluated in the cloud if you use Microsoft Defender ATP which is part of Windows 10 Enterprise E5. Keep in mind that some sub-features of Exploit Guard regarding monitoring are also exclusive to Microsoft Defender ATP.
- Use Windows Hello for Business for passwordless sign-in (PIN or biometry + TPM)
- Deprecate legacy protocols like SMBv1 and LM/NTLM
- Use all those Windows 10 security features to build Privileged Access Workstations (PAWs) for cloud and on-prem administration.
Disclaimer: This overview was created to the best of my knowledge. It might be suspect to change at any time, especially if Microsoft changes licensing. I do not guarantee that this is a comprehensive overview.

Thanks for reading!
Chris

OFFICE 365 Enterprise E3 Account




