Network Level Authentication (NLA)
- Nla Rdp Windows 10 To Windows 7
- Nla Rdp Windows 10 Sounds
- Remote Desktop With Nla
- Best Rdp For Windows 10
This blog post is divided into two sections: the first section relates to the machines Without RD Session Host Role, while the second part refers to the machines With RD Session Host Role.
These two sections are further divided into different Operating Systems to choose from.
This post shows how to disable network-level authentication to allow for RDP connections on a target device.
Quick Links
- Windows 10 Fall Creator Update (1709) or later You can configure your PC for remote access with a few easy steps. On the device you want to connect to, select Start and then click the Settings icon on the left. Select the System group followed by the Remote Desktop item.
- RDP will now be enabled on your system. All appropriate changes to the firewall will also be made automatically. To start a Remote Desktop Connection, Hold Windows key and Press R.Type mstsc and Click OK. Type the computer name or IP address of the system you are going to access and click Connect. Make sure the account through which you are going to access a system remotely has a.
Disabling Network Level Authentication without RD Session Host Role
To fix The remote computer requires Network Level Authentication error in Windows 10/8/7, you must have to disable or turn off Network Level Authentication (NLA). Otherwise, this is not possible to connect to the remote computer even if both machines are in the same Local Area Network. You can try any aforementioned method to disable NLA.
Windows 7 & Windows Server 2008/Windows Server 2008 R2
- Open the Control Panel. Ensure that the control panel is showing items by Category (i.e., not in Classic View). Click on System and Security and under System click on Allow remote access.
- Under the Remote Desktop group, select Allow connections from computers running any version of Remote Desktop (less secure).
Windows 8 and Windows Server 2012/Windows Server 2012 R2
- Open the Control Panel. Ensure that the control panel is showing items by Category. Click on System and Security and under System click on Allow remote access.
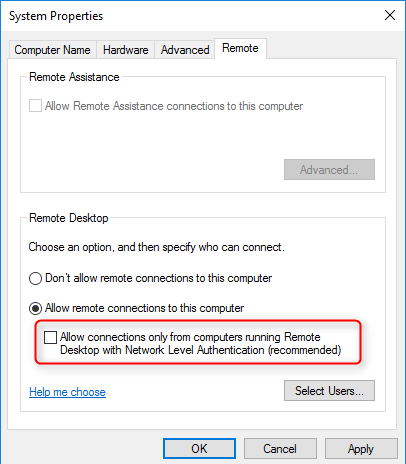
- Under the Remote Desktop group deselect the option Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)
Windows 10 & Windows Server 2016
- Open the Control Panel. Ensure that the control panel is showing items by Category (i.e., not in Classic View). Click on System and Security and under System click on Allow remote access.
- Under the Remote group choose Allow remote connections to this computer.
Disabling Network Level Authentication with the RD Session Host Role
In Windows 2008 and Windows 2008 R2
- On the RD Session Host server, open Remote Desktop Session Host Configuration. To do this, click Start, point to Administrative Tools, point to Remote Desktop Services, and then click Remote Desktop Session Host Configuration.
- Under Connections, right-click the name of the connection, and then click Properties.
- On the General tab, un-tick the Allow connections only from computers running Remote Desktop with Network Level Authentication check box. (For maximum compatibility ensure that Security Layer is set to Negotiate)
If the Allow connections only from computers running Remote Desktop with Network Level Authentication check box is selected and is not enabled, the Require user authentication for remote connections by using Network Level Authentication Group Policy setting has been enabled and applied to the RD Session Host server.
- Click OK.
Windows 2012/Windows Server 2012 R2 & Windows Server 2016/2019
- On the RD Session Host server, open the Server Manager.
- Click on Remote Desktop Services, then under Collections click on the name of the session collection name that you want to modify. Click on Tasks and select Edit properties.
- Under the Security tab un-tick the option Allow connections only from computers running Remote Desktop with Network Level Authentication. (For maximum compatibility ensure that Security Layer is set to Negotiate)
If the Allow connections only from computers running Remote Desktop with Network Level Authentication check box is selected and is not enabled, the Require user authentication for remote connections by using Network Level Authentication Group Policy setting has been enabled and applied to the RD Session Host server. Cause
There are multiple reasons why NLA might block the RDP access to a VM:
- The VM cannot communicate with the domain controller (DC). This problem could prevent an RDP session from accessing a VM by using domain credentials. However, you would still be able to log on by using the Local Administrator credentials. This problem may occur in the following situations:
- The Active Directory Security Channel between this VM and the DC is broken.
- The VM has an old copy of the account password and the DC has a newer copy.
- The DC that this VM is connecting to is unhealthy.
- The encryption level of the VM is higher than the one that’s used by the client computer.
- The TLS 1.0, 1.1, or 1.2 (server) protocols are disabled on the VM.The VM was set up to disable logging on by using domain credentials, and the Local Security Authority (LSA) is set up incorrectly.
- The VM was set up to accept only Federal Information Processing Standard (FIPS)-compliant algorithm connections. This is usually done by using Active Directory policy. This is a rare configuration, but FIPS can be enforced for Remote Desktop connections only.
Before you troubleshoot
Create a backup snapshot
To create a backup snapshot, follow the steps in Snapshot a disk.
Connect to the VM remotely
To connect to the VM remotely , use one of the methods in How to use remote tools to troubleshoot Azure VM issues.
Group policy client service
If this is a domain-joined VM, first stop the Group Policy Client service to prevent any Active Directory Policy from overwriting the changes. To do this, run the following command:
After the problem is fixed, restore the ability of this VM to contact the domain to retrieve the latest GPO from the domain. To do this, run the following commands:
If the change is reverted, it means that an Active Directory policy is causing the problem.
Workaround
As a work around to connect to the VM and resolve the cause, you can temporarily disable NLA. To disable NLA please use the below commands, or use the
DisableNLAscript in Run Command.Then, restart the VM, and proceed to the troubleshooting section.
Once you have resolved the issue re-enable NLA, by runing the following commands, and then restarting the VM:
Troubleshooting
Troubleshoot Domain-joined VMs
To troubleshoot this problem:
- Check whether the VM can connect to a DC.
- Check the health of the DC.
Note
To test the DC health, you can use another VM that is in the same VNET, subnet, and uses the same logon server.
Connect to the VM that has the problem by using Serial console, remote CMD, or remote PowerShell, according to the steps in the Connect to the VM remotely section.
Determine the DC that the VM is attempting to connect to. run the following command in the console:
Test the health of the secure channel between the VM and the DC. To do this, run the
Test-ComputerSecureChannelcommand in an elevated PowerShell instance. This command returns True or False indicating whether the secure channel is alive:If the channel is broken, run the following command to repair it:
Make sure that the computer account password in Active Directory is updated on the VM and the DC:
If the communication between the DC and the VM is good, but the DC is not healthy enough to open an RDP session, you can try to restart the DC.
If the preceding commands did not fix the communication problem to the domain, you can rejoin this VM to the domain. To do this, follow these steps:
Create a script that’s named Unjoin.ps1 by using the following content, and then deploy the script as a Custom Script Extension on the Azure portal:
This script forcibly removes the VM from the domain and restarts the VM 10 seconds later. Then, you need to clean up the Computer object on the domain side.
After the cleanup is done, rejoin this VM to the domain. To do this, create a script that is named JoinDomain.ps1 by using the following content, and then deploy the script as a Custom Script Extension on the Azure portal:
Note
This joins the VM on the domain by using the specified credentials.
Nla Rdp Windows 10 To Windows 7
If the Active Directory channel is healthy, the computer password is updated, and the domain controller is working as expected, try the following steps.
If the problem persists, check whether the domain credential is disabled. To do this, open an elevated Command Prompt window, and then run the following command to determine whether the VM is set up to disable domain accounts for logging on to the VM:

If the key is set to 1, this means that the server was set up not to allow domain credentials. Change this key to 0.
Troubleshoot standalone VMs
Check MinEncryptionLevel
In an CMD instance, run the following command to query the MinEncryptionLevel registry value:
Based on the registry value, follow these steps:
4 (FIPS): Go to Check FIPs compliant algorithms connections.
3 (128-bit encryption): Set the severity to 2 by running the following command:
2 (Highest encryption possible, as dictated by the client): You can try to set the encryption to the minimum value of 1 by running the following command:
Restart the VM so that the changes to the registry take effect.
Nla Rdp Windows 10 Sounds
TLS version
Depending on the system, RDP uses the TLS 1.0, 1.1, or 1.2 (server) protocol. To query how these protocols are set up on the VM, open a CMD instance, and then run the following commands:
If the returned values are not all 1, this means that the protocol is disabled. To enable these protocols, run the following commands:
For other protocol versions, you can run the following commands:
Note
Get the SSH/TLS version x.x from the Guest OS Logs on the SCHANNEL errors.
Check FIPs compliant algorithms connections
Remote desktop can be enforced to use only FIPs-compliant algorithm connections. This can be set by using a registry key. To do this, open an elevated Command Prompt window, and then query the following keys:
If the command returns 1, change the registry value to 0.
Remote Desktop With Nla
Check which is the current MinEncryptionLevel on the VM:
If the command returns 4, change the registry value to 2
Restart the VM so that the changes to the registry take effect.
Best Rdp For Windows 10
Next steps

- The VM cannot communicate with the domain controller (DC). This problem could prevent an RDP session from accessing a VM by using domain credentials. However, you would still be able to log on by using the Local Administrator credentials. This problem may occur in the following situations:



